Our Comprehensive Guide on How to Implement Automated Incident Response

Quick Summary
We explore the essential steps to implement a successful automated incident response, from defining incidents to optimizing systems. Alongside powerful features from Instatus like real-time monitoring and status updates, you’ll learn how to build a proactive system that keeps teams focused and users informed. Explore further resources on our blog for more guidance.
Looking to Automate Your Incident Responses?
Automated incident response can help companies resolve data breaches up to 30% faster, according to BusinessWire. By reducing manual intervention and streamlining the process of managing and resolving incidents, automation boosts response speed and efficiency.
But how can you implement this in your own organization?
In this Instatus guide, we’ll outline 5 effective ways to implement automated incident response. But first, let’s take a closer look at what’s involved.
Why Listen to Us?
At Instatus we help teams manage and communicate IT issues with ease. Designed for SaaS, DevOps, and developer teams, our customizable status pages and real-time monitoring integrations mean fewer support tickets and more trust with users.
By providing granular control over security and access, we believe that an efficient incident response isn’t just reactive— it’s preventive.
What Is Automated Incident Response?
Automated incident response is the use of software and workflows to detect, assess, and resolve IT incidents with minimal human intervention. It integrates monitoring, alerting, and response actions to ensure quick resolutions and reduce downtime.
With automated incident response, you can handle repetitive tasks systematically, reducing human error and freeing your teams to focus on critical decision-making. It leverages predefined rules and machine learning to recognize patterns, prioritize incidents, and execute response steps instantly.
Why Is Automated Incident Response Important?
- Faster Response Times: Automation enables instant action on incidents, reducing downtime and minimizing service disruptions.
- Reduced Human Error: By automating repetitive tasks, we eliminate common human errors, ensuring consistency and reliability in responses.
- Scalability: Automated systems can handle high volumes of incidents, allowing us to manage complex environments without overwhelming teams.
- Cost Savings: Streamlining responses reduces the resources and time spent on manual intervention, optimizing operational costs.
5 Effective Ways to Implement Automated Incident Response
Step 1: Identify and Define Incident Types
Defining incident types is foundational for setting up a responsive, automated incident response system. At this stage, categorize incidents based on severity, impact, and frequency, ensuring automation aligns with the specific needs of each type.
Action Steps:
-
Review Past Incidents: Analyze trends, patterns, and recurring issues to define incident types.
-
Use Data Insights: For instance, Instatus’s incident updates can provide valuable data on the duration, impact, and resolution of past incidents.
-
Features of Instatus Incident Updates:
- Retrieve specific incident updates
- Add new updates with status and translation options
- Edit or delete updates
- Resolve incidents with templates
-
Defining Parameters:
- Triggers: Specify event patterns, thresholds, or conditions (e.g., a continuous 500-error rate or response times exceeding acceptable limits).
- Impact Levels: Define the scope of impact, such as critical incidents that affect multiple systems versus lower-impact incidents affecting isolated processes.
- Automation Priorities: Decide which incidents require immediate automated responses and which require further review.
Once the categories are defined, create a table or database to document each incident type’s details. This centralized reference ensures consistency across your automation workflows.
Validation: Work with cross-functional teams to ensure these categories align with operational needs.
Step 2: Select and Configure Automation Tools
Choosing the right automation tools is critical for a streamlined incident response system. Consider factors like:
- Seamless Integration: Ensure compatibility with your existing monitoring systems. For example, we can integrate with tools like Datadog and Pingdom, allowing incidents from these systems to trigger alerts automatically on your status page.

- Customizable Alerts and Actions: Choose tools that allow detailed configuration of alerts, response rules, and escalation paths.
- Real-Time Monitoring: Opt for tools with continuous monitoring and minimal lag. This ensures that incidents are detected immediately, triggering automated responses as needed.
Configuration Steps:
- Map your incident categories and priorities to the selected automation tools.
- Configure predefined rules to automate notifications, responses, and escalations.
- Test these configurations in simulated scenarios to confirm reliability.
Step 3: Develop and Test Response Workflows
Creating good response workflows is essential to ensure automated responses are accurate and effective. For each incident type, outline a step-by-step response plan that guides the system through detection, notification, escalation, and resolution actions.
Define key actions for each workflow, such as:
- Initial Detection and Verification: Specify how the system should validate the incident before proceeding, such as cross-checking multiple alert sources to confirm legitimacy.
- Notification and Escalation: Map escalation paths and set thresholds for when and how alerts are routed. We support on-call schedules and escalation rules, ensuring incidents are routed to the correct teams immediately.
- Automated Response Actions: Outline specific actions for resolution like restarting services, applying predefined fixes, or isolating affected components. Customize these actions based on the incident’s severity.
Testing: Test workflows under simulated incident conditions to identify bottlenecks or delays. Test edge cases to ensure robustness. Regularly review and update workflows based on performance data and feedback.
Step 4: Set Up Monitoring and Alerts
Effective monitoring and alerting ensure that incidents are detected immediately, allowing automated responses to initiate without delay. Configure monitoring to capture performance metrics, error rates, and any anomalies that could indicate an issue.
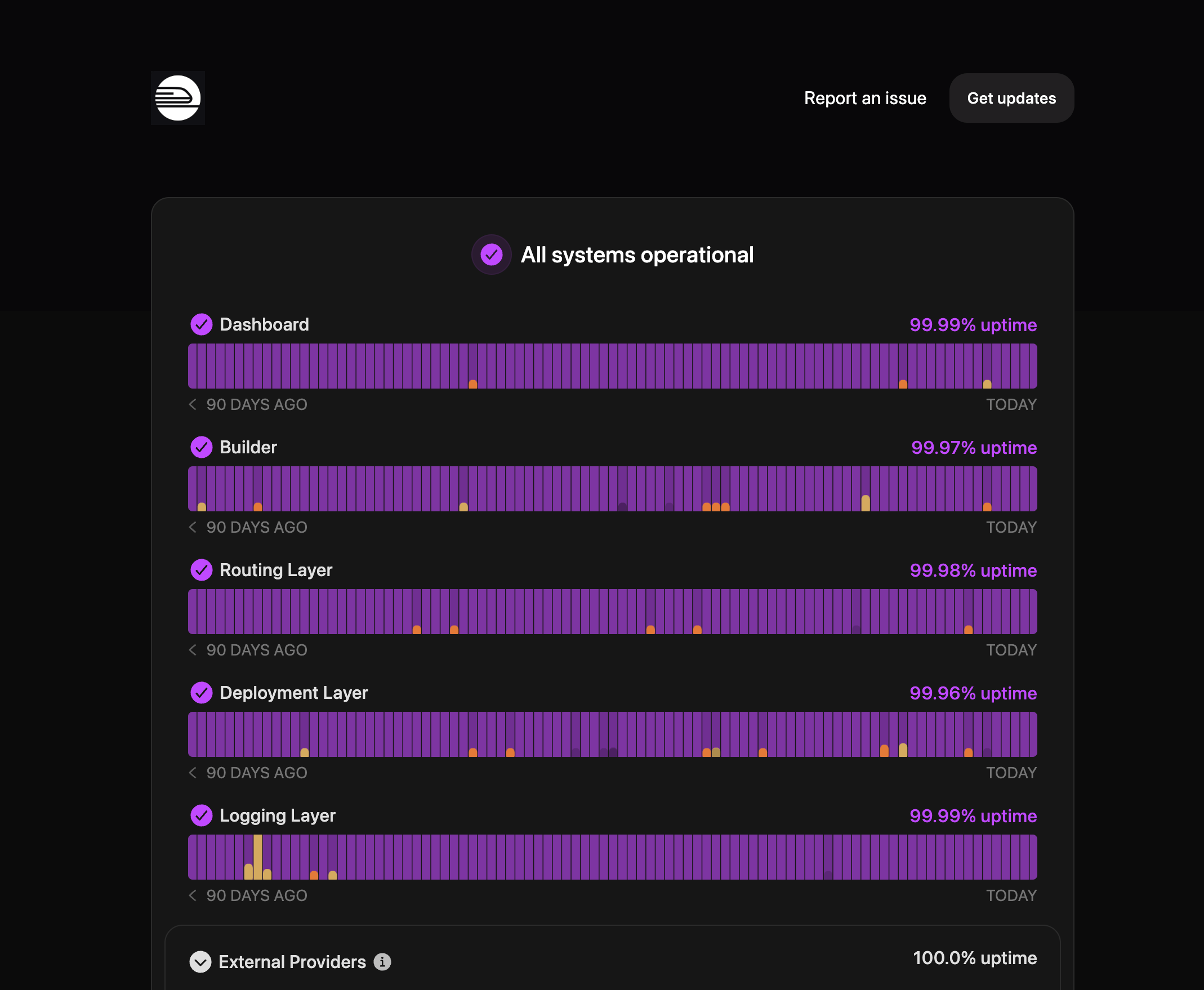
Our monitoring features, including API, keyword, CRON, ping, SSL, TCP and DNS checks every 30 seconds, can provide the real-time visibility your team needs to spot incidents early. You can adjust monitor states to reflect current operational statuses and set up category-specific monitoring.
It supports a variety of status updates, ideal for real-time service monitoring and transparency for stakeholders.
When setting up alerts, ensure they are:
- Granular: Configure alerts to target specific issues, reducing false positives. For instance, alert only on sustained downtime rather than momentary blips.
- Prioritized: Assign severity levels to incidents. Critical incidents might trigger high-priority alerts, while lower-impact events generate less intrusive notifications.
- Integrated with Automation: Link alerts to your automated workflows. Instatus notifications can automatically escalate to the appropriate team, ensuring immediate attention.
Alert Configuration:
- Set up thresholds that balance responsiveness with noise reduction, ensuring critical incidents are promptly addressed.
- Use alert routing to send notifications to specific channels (e.g., Slack, email) based on incident severity and team responsibilities.
For instance, our Slack integration lets you send real-time status updates to your Slack workspace, keeping your team informed on incidents and updates, and streamlining communication during any incidents.

Testing: Regularly test alerting and routing systems to ensure they function as expected. Simulate incidents to validate that alerts are properly triggered, and automated actions follow.
Step 5: Review and Optimize Regularly
To maintain effective automated incident response, set a routine for reviewing and optimizing workflows, alerts, and response strategies. Regular reviews ensure your setup adapts to evolving incidents and operational changes.
Start by analyzing incident data. And our status page insights can help with that by revealing patterns in incident frequency, response times, and common issues. DevOps teams, for example, can reduce ticket volume by providing customers a clear, centralized place to check the system’s status before they even reach out.
Our status pages also support 21 languages, so your international customers always have access to important updates in their language.
Use these insights to identify areas where your workflows can improve, like reducing response delays or removing redundant steps.
Review these key areas:
- Workflow Efficiency: Look for bottlenecks in escalation paths and response actions. Streamlining complex steps can improve resolution times.
- Alert Relevance: Adjust alert thresholds and conditions based on feedback and incident history, minimizing noise while maintaining accuracy.
- Response Accuracy: Regularly test automated actions to ensure they’re aligned with current incident types and don’t trigger unnecessary responses.
Incorporate these optimizations back into your system, creating an adaptive, resilient response strategy.
6 Best Practices for Implementing Automated Incident Response
- Classify Incidents Clearly: Categorize incidents by type and severity to ensure automated responses are appropriate to the impact.
- Select the Right Tools: Choose automation tools that integrate seamlessly with your monitoring and incident management systems.
- Balance Automation with Human Oversight: Use automation for repetitive tasks, but allow human intervention for complex or high-impact incidents.
- Design for Flexibility: Build adaptable workflows that can evolve with new incident types or infrastructure changes.
- Regularly Review and Refine: Continuously evaluate and improve automated workflows to keep pace with changing needs and technologies.
- Ensure Transparency: Integrate automated systems with communication tools to provide real-time updates to internal teams and customers.
Automate Your Incident Responses Better with Instatus
Automated incident response enhances efficiency, reduces downtime, and ensures consistent handling of critical issues. With Instatus, these steps become even more effective.
Our solid monitoring, status updates, and incident management features tailored for automated response systems keeps both your team and users informed in real time, enhancing transparency and trust.
Why wait? Start free at Instatus today and take your incident response to the next level.
Get ready for downtime
Monitor your services
Fix incidents with your team
Share your status with customers